Cybersecurity on SAP: an Active and Necessary Step
Companies spend millions of dollars on firewalls, encryption, and secure access devices, and it’s money wasted, because none of these measures address the weakest link in the security chain. Kevin Mitnick, Famous Hacker
Kevin Mitnick, Famous Hacker - Economist.com
The disaster of USIS
Cyber security incidents regularly grab the headlines. As such, no sector of activity nor technology are spared. Indeed, SAP systems, which have not been attacked for a long time, are now also targeted.
 Photo credit : Infosecurity magazine
Photo credit : Infosecurity magazine
In 2013, the United States Information Service (USIS), a subcontractor of the US federal government, also responsible for security checks of government employees, was hacked. Chinese hackers exploited a vulnerability to access thousands of files related to employees (Reuters). This lasted several months before the intrusion was detected (The Hill). Needless to say, this was a huge scandal that was publicly discussed in the US Congress. The economic and human consequences are disastrous for the USIS: its contracts with the US federal government are abruptly broken, 2,500 employees were dismissed, and the parent company declared bankruptcy (Bloomberg, The Washington Post , ERP scan).
 The USIS website, which does not exist anymore
The USIS website, which does not exist anymore
Although the technical details of the breach have never been revealed, the lesson to be learned is that no system is immune. In the case of USIS, the technical security infrastructure did not prevent or even detect the intrusion for up to six months.
Systems called "internal", "isolated from the internet" or "secured by firewalls", often mentioned by the administrators, do not guarantee their inviolability. Cyber security is an active approach which has a human factor at its heart. Indeed, network experts, developers, SAP consultants, and end users all have their role to play. The biggest risk is to underestimate the risks.
ERP applications as targets
On July 25, 2018, the US-CERT (branch of the Homeland Security department, responsible for cybersecurity) (Wikipedia) has issued an alert advising the presence of known vulnerabilities in ERP applications, including SAP and Oracle. The latter had become privileged targets for pirates.
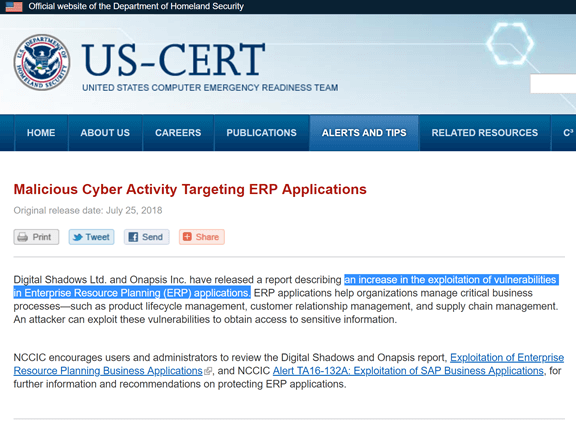 Photo Credit: Official Website of the Department of Homeland Security
Photo Credit: Official Website of the Department of Homeland Security
The US-CERT report has raised a drastic increase in the exploitation of vulnerabilities in ERP applications, with a 160% increase from 2016 to 2017. In addition, the latter emphasizes that in the majority of cases, vulnerabilities exploited are not new; rather, they are old ones for which patches exist but never have been applied (Infosecurity-magazine).
This is a problem that goes beyond ERP. Cyber security goes far beyond managing roles and user profiles. For example, many SAP web servers (ABAP and J2EE) are rarely updated by administrators, making them a prime target for malicious people (PCWorld).
Solutions exists, we need to apply them
Facing repeated security incidents and warnings, nothing is “fatal”. For several years, SAP has significantly improved the safety of its products:
- SAP Security Patch Day: On the second Tuesday of each month, SAP publishes a list of SAP notes of new vulnerabilities discovered, ranked by criticality. It is even possible through the Solution Manager configuration to automatically filter the relevant SAP notes for each customer, based on the products deployed.

- Regularly update SAP systems (at least once a year). SAP ecosystems are often complex and require very high availability. However, when carefully planned, an SAP Support Packages campaign has a limited impact on user activity.
- Configuration of Single-Sign-On (SSO): One of the most frequently used attack axes: SAP passwords are removed. Internally, this can be done via the SAP SSO 3.0 solution. For external connections, SAML 2.0 will need to be deployed.
Configuration du SAML2 sur un système SAP S/4HANA
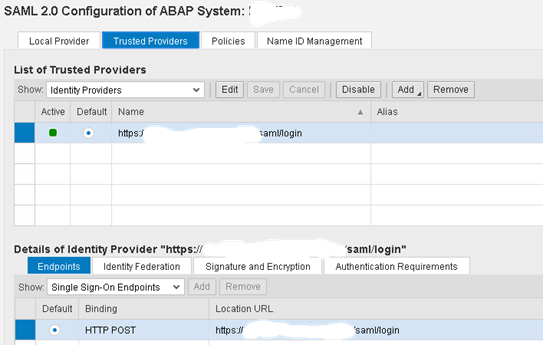 SAML 2 Configuration on a SAP S/4HANA System
SAML 2 Configuration on a SAP S/4HANA System
- Encrypt communications between the SAP server and clients (SAP GUI or Fiori Launchpad) via SNC (Secure Network Communication: SAP note 2440692) Activating Access Control Lists (ACLs)
- Secure Remote Function Call (RFC) destinations. RFC Links are often considered the Trojan horse of SAP infrastructures. Moreover, in the above-mentioned case of the USIS, there is strong suspicion towards an unsecure RFC destination (ERPscan, Onapsis), as well as to the use of default SAP technical users that will need to be deactivated.
- Secure access to the database. Security settings are specific to each database. In the case of HANA, security has been at the heart of its design: SAP note 2159014. Features are many. They include antiviruses: 1730930, 1969700 security check scripts, 2444090 backup encryption, 2127458 data encryption, and 1761693 database connection encryption.
- Securing SSL parameters and the supported cryptographic suite: Encryption algorithms constantly under attack, are regularly improved: sap notes 510007, 2570499. It is therefore necessary to regularly check the Cryptographic suite to use, and if necessary readjust.
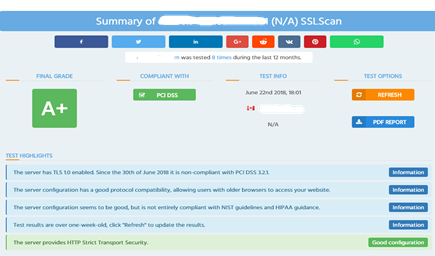 SSL control of a compliant SAP S/4HANA compliant with Payment Card Industry (PCI) requirements
SSL control of a compliant SAP S/4HANA compliant with Payment Card Industry (PCI) requirements
The options are many. This is not an exhaustive list of possibilities for securing and fortifying an SAP infrastructure. Createch can help you to evaluate the security of your SAP systems, as well as suggest and implement improvements.
Download our whitepaper "Migration to SAP S/4HANA > By 2027, all SAP customers must have migrated to the SAP HANA database. The infrastructure is therefore an excellent starting point to think about its roadmap."







